For a developer skimming through the datasheets of the latest microcontrollers, it’s easy to assume that efficient use of CPU resources, including memory and clock cycles, is, at most, a minor concern with today’s hardware. The latest 32-bit MCUs offer flash memory and RAM allocations that were unheard of in the embedded space just a short time ago, and their CPUs are often clocked at speeds once reserved for desktop PCs. However, as anyone with recent experience developing a product for the IoT knows, these advances in hardware have not occurred in a vacuum; they have been accompanied by pronounced changes in end-user expectations and design requirements. Accordingly, it is perhaps more important now than ever for developers to ensure that their software runs with the utmost efficiency and that their own time is spent in an efficient manner.
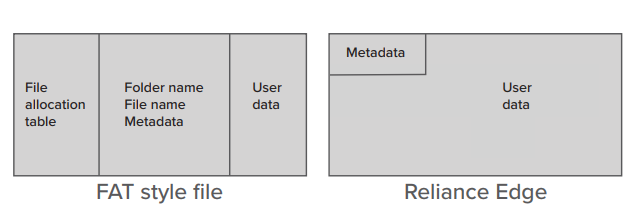
FAT vs Reliance
The software running on modern embedded systems tends to come from a variety of sources. Code written by application developers is often combined with off the-shelf software components from an RTOS (real-time operating system) provider, and these components may, in turn, utilize driver code originally offered by a semiconductor company. Each piece of code can be written to optimize efficiency, but this article will focus on efficiency within off-the-shelf software components. Two components in particular will serve as the foundation for the examination of resource efficiency given herein: a real-time kernel and a transactional file system.
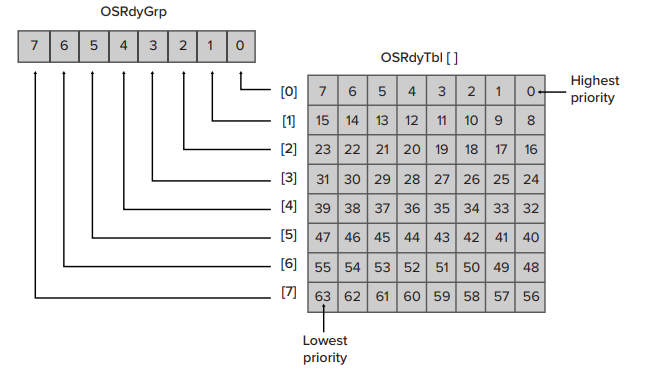
In the Cs/OS2 scheduler, each task priority is represented by a bit in an array.
What type of development environment might be present in an IoT project? Given the rapidly growing demand for connectivity in embedded devices, it’s impossible to identify one particular combination of hardware, software, and tool-chain that defines the space. It’s similarly challenging to find a single end product that fully represents the range of possibilities in IoT. Nonetheless, discussions in this field can certainly benefit from concrete examples which will be discussed in the Whitepaper by Thom Denholm (Tuxera) and Matt Gordon (formerly Micrium).

Gevorg Melikdjanjan
Security | Reliability | Data Solutions