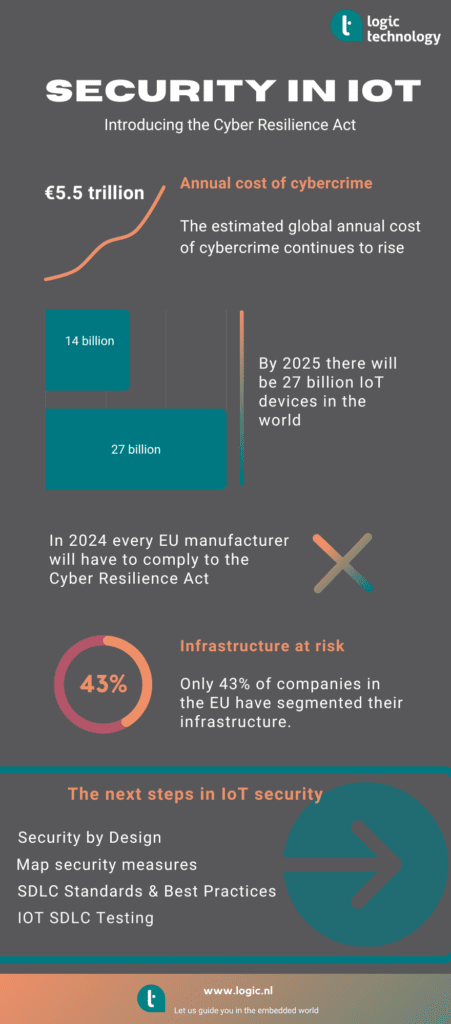
By 2024 any IoT or smart device sold in the EU must meet certain standards or the product will be banned from the EU market. In November 2019, the European Union Agency for Cybersecurity, “enisa”, released a study on Good Practices for Security of IoT – Secure Software Development Lifecycle” bringing together the views on best Secure SDLC practices from industry leaders from all over the world to make European manufacturers of smart connected devices aware of the eminent threats of hacks and cybercrimes and their danger for infrastructure and economies.
This study laid the groundwork for EU President von der Leyen to proclaim the European Cyber Resilience Act aimed at setting common cybersecurity standards for connected devices announced in September 2021. In October of the same year the European Commission adopted the Delegated Act on Cybersecurity to the Radio Equipment Directive (RED) and one month later the word was out: “by 2024 any IoT or smart device sold in the EU must meet certain standards or the product will be banned from the EU market”.
Since then the industry and consumer organizations have tried to formalize legislation and EU ministers will meet to discuss the Act for the time on December 6, 2022.
In the mean time the clock is ticking, not the least for organizations actively involved in development, deployment, maintenance and infrastructure. And although big steps have been taken since the release of the enisa study in 2019, it is frightening to see that only 43% of companies in the EU have segmented their infrastructure since in an effort to reduce risks of cyber threats. There is still plenty of open playing fields for cyber attackers until 2024 and most likely beyond.
4 proven strategies for IoT security
- Security by Design
- Map security measures
- SDLC Standards & Best Practices
- IOT SDLC Testing
Security by Design
Security is a joined responsibility of hardware and software developers; A secure design starts at the hardware level and thus influences the design of the software. A good example is the use of a Trusted Platform Module in the hardware where the private key of a cryptographic algorithm, used in a software stack, is held. Another, slightly less secure, method is the use of an encrypted vault in a secured part of flash memory.
Map security measures
An important aspect of any type of process implementation is that of its constant assessment and evaluation. Security Maturity Models help organizations to align the level of security with their requirements. The assessment should also align with industry compliance requirements and related standards. Which
SDLC Standards & Best Practices
It goes without saying that Standards and Best Practices are intertwined and involve People, Processes and Technologies. Each of which require a specific set of security measures. People can be trained and made aware of security, vulnerability and responsibility. Processes manage the organization, SDLC methodology, design and deployment whilst Technologies provide the means used to reduce vulnerabilities and bugs during the development process.
IOT SDLC Testing
Testing is a major aspect of any product development, but especially when security is a requirement. Industry standards aid in reaching a reasonable level of reliability and security but are foremost used to certify compliance to the standard. There are many ways of testing software: static and dynamic testing, formal testing, manual or automated testing. Depending on the industry, code complexity and other metrics it is important to assess the particular needs of the software and establish the most suitable and efficient testing strategy and testing environment during the testing phase.
In summary, developing secure and reliable devices requires careful planning and tuning of people, processes and technologies. Fortunately, there are many guidelines, standards and tools available to assist in achieving the highest level of security for many industries.

Gilbert Gadet
UEFI | BIOS | General Information
If you need advice on creating (additional) security in your IoT products, I'm happy to help!